Raising The Process Compliance Bar
Designing controls in business processes is not a new concept. Over the decades, there are numerous regulations and policies requiring corporations to identify the financial and operational risks inherent to their business processes and establish the appropriate controls to address them.The excuse of “mistakes” in processes, particularly regarding checks and controls in this case, is hardly acceptable in the modern day and age of technological advancement and the cry of process excellence in corporations.
Although there are checks and controls in most of the enterprise processes across industries, especially those that are highly regulated, not to mention those that aspire to be process excellence, it is unfortunately common to see the failure of these checks and controls. For instance, steps that are critical controls are missed, circumvented, or performed as an after the fact activities. In short, it is a ‘process compliance’ issue in business process management practice.
Before jumping into the deep end of process compliance, let’s revisit two main sources that cause the process compliance gap in most corporations - First, the established process models in repository versus runtime processes; second, the business processes versus business information systems;
Process Model versus Process Runtime Execution
In an article (2013) I wrote, I have briefly discussed about the differences on the many terms used between process, process definition and process model, but stopped at looking into the consequence of the misunderstanding.Although it is a good practice and an essential step in process oriented management to establish a central repository of enterprise process models, it is crucial to understand that a process model is only a representation of the scenarios and activities. In other words, it is only representing the modeled behaviour or ‘expected’ behaviour rather than an ongoing observed behaviour during runtime execution. So in the case of a control activity that is mapped on a process model, it does not mean that the activity is executed and enforced in every instance of that process.
Most business process models are mapped without relating to data in the business information systems. In other words, for most business processes without a BPMS or WMS the process models and the data generated by the business information systems are at best loosely coupled.
Business Process Management System and Workflow Management System are exception to this discrepancy where such connection is built into these systems. Process aware systems are hence important for process automation and also serve as a powerful enabler for continuous process analysis and improvement.
In general, it is the goal of for business to achieve an alignment between the many business information systems running in the business and its business processes. However, off-the-shelf software commonly adopted by corporations is based on so-called “best practices”. This “best practice” are normally predefined procedures and scenarios that are implemented based on given conditions which were accepted by the software developer at the point of development, very likely for other business operating is very different ‘conditions’. These conditions in most cases do not align to the operating conditions of the corporations acquiring the software. The consequence of such adoption is where workers that should be supported by the business information systems, work behind the systems to get things done rightly or wrongly.
Another source of the misalignment is the conflicting requirements of the stakeholders during software implementation, such as a fixed procedures from a manager’s view versus a more flexible solution from the view of an experienced worker.
Moreover, in the ever changing internal landscape and external environments, business processes inevitably have to make changes before the change is implemented on the business information systems. Hence again forcing workers to work around the systems.
Limitation of Internal Audit
Internal auditing as part of assurance service and business process review is commonly used as a mean to assess the business operations, including its business processes. It includes checking the operating effectiveness of controls that are designed to ensure reliable conformance. These internal audit typically only check samples of the data and sometimes purely based on interviews with process participants and/or process owners. This can only provide reasonable assurance with limited scope that the business processes are executed within the given set of boundaries. It is not equipped to be a bloodhound that sniff out every single case where these controls are not in place, or otherwise not functioning as expected.Process Compliance Assurance Using Process Mining
In the modern day business information systems, detailed information about business operations and processes is being recorded in the form of event logs, transaction logs and system audit trails, which are stored in databases of business information systems and data warehouses. Using process mining tool, such as Apromore, various methods can be used to establish a tight coupling between the process models and these logs, allowing all these records related to a business process be evaluated.With proper integration, it also allows real time process compliance monitoring, that is evaluating the runtime process even while the process is still running. The advancement in process mining analytics also opens up opportunity in developing of predictive process monitoring.
“Process mining is a family of techniques used to analyse the performance and conformance of business processes, based on transactional data recorded by common IT systems within an organisation,” Professor Marcello La Rosa, School of Computing & Information Systems, The University of Melbourne
 |
| Figure 1: Process conformance checking between event and transaction logs and modeled process |
Process conformance checking as illustrated in Figure 1 is the comparing of observed behaviour with modeled behavior on a process model using process mining techniques (Wil van der Aalst, 2016). Data extracted from the event log and transaction log may be projected onto the process model to show deviations, discrepancies, bottlenecks and frequent paths - showing global conformance measures that quantify the overall conformance of the event and transaction log and the process model. Local diagnostics can be performed on individual cases with discrepancies, highlighting the activities in the process model where the log and model mismatch (see Figure 2).
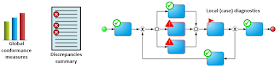 |
| Figure 2: Global conformance measures, discrepancies and local (case) diagnostics |
A process conformance checking exercise using process mining technique will reveal undesirable deviations between the runtime execution log and the established process model. Such deviations provide indicators on which part of the process needs redesigning to ensure better and more effective control.
 |
| Figure 3: Conformance measures in percentages (courtesy of Prof. M. L. Rosa) |
 |
| Figure 4: Local (case) diagnostics of mismatched activities (courtesy of Prof. M. L. Rosa) |
The activities captured in the log are overlaid on the enterprise process model with any deviations highlighted. The deviations identified from a process conformance checking could provide insight on either an indication that the process model is wrong and does not reflect current operation; or the case in question has deviated from the process model (desired behaviour).
The first insight would trigger an initiative to update the process model and ensure the controls are still in place to meet regulatory and policy requirements. In the later insight, it should trigger an alert on non compliance behaviour where corrective actions are needed to improve the control in place and ensure higher degree of conformance.
The ultimate outcome of a continuing process mining exercises will ensure a real transparency of the business operations and its business processes, auditability in greater scope and granularity; and in-time intervention when and where needed.
Process mining techniques can play an important role in term of compliance checking and monitoring - to relate observed behaviour from business information system log to modeled behaviour of process model. It also open up opportunities on detecting and diagnostics of deviations to trigger alert and intervention. It uses event and transaction data to “breathe life” into otherwise static process models sitting in process repository. With the more stringent regulatory requirements putting process owners in banking and financial industry under the spotlight, the application of process mining to not only support better internal audit, but also enabling a continuous monitoring to provide process compliance assurance is inevitable.
Note on Apromore
Apromore is an open-source, online business process analytics platform, supporting a range of state-of-the-art process mining features, from automated process discovery through to performance mining, conformance checking, variants analysis and predictive process monitoring. Headquartered at the University of Melbourne and supported by the University of Tartu (Estonia), Apromore is the result of over ten years of research and development, with contributions from different universities and funding from the government and private sector. In addition to being a full-spectrum process mining tool, Apromore also provides a process modeling environment via integration with two third-party open-source tools: BPMN.io and Signavio core components.Website: http://apromore.org/
Project leaders: Professor Marcello La Rosa (University of Melbourne) and Professor Marlon Dumas (University of Tartu)
Reference
- Professor Elise Bant, 2019, “The Buck Stops Here: Holding Banks Responsible For Dishonest Conduct”, URL [link]
- Ilya Verenich, 2019, “Explainable Predictive Monitoring of Temporal Measures of Business Processes”, URL [link]
- Professor Marcello La Rosa, 2018, “How open-source software is helping business improve its processes”, URL [link]
- Professor Wil van der Aalst, 2016, Process Mining: Data Science in Action, 2nd Edition, Springer
Max
ReplyDeleteInteresting and relevant to my recent article in ICAS CA magazine - basically accountants are now well placed to help business regain control (thus compliance) over their operational processes. Your view further enhanced by fact the model can now be runtime application with full audit trails of who did what when. Drop me email at david.chassels@btinternet.com and will send copy